How It Works
This connector creates a secure bridge between your S3 buckets and Cloudglue:- Direct S3 access - We only access your files when you explicitly use them
- No manual uploads - Skip the process of manually uploading files to Cloudglue
- S3 URI support - Use your existing S3 URIs directly with Cloudglue endpoints
Security
Security is paramount, so we use AWS best practices with cross-account IAM roles. You’ll create an IAM role in your AWS account that Cloudglue can assume to access your buckets. This approach:- Maintains your control - You own and manage the role
- Follows AWS security patterns - Uses standard cross-account role assumption
- Provides granular permissions - Only grants the minimum access needed
- Easy to revoke - Simply delete the role or modify permissions
Setup Options
Option 1: CloudFormation Template (Recommended)
We provide a CloudFormation template that automates the entire setup process:- Copy and deploy the template in your AWS account
- Provide us the role ARN that gets created
- Configure the connector on our web platform
The CloudFormation template handles all the IAM role creation, policies, and
trust relationships automatically.
CloudFormation Template
For your convenience, you can download the template here.View template contents
View template contents
- Download the template
- Navigate to the CloudFormation console in your AWS account
- Click on the Create stack button
- Select Upload a template file
- Upload the template you downloaded
- Set your bucket name parameter
- Deploy the stack
Option 2: Manual Setup
If you prefer manual configuration, you can create the required IAM role and policies yourself: To create the role:- Navigate to the IAM console
- Click on the Roles, under Access management
- Click on the Create role button
- Select AWS account as the trusted entity
- Under An AWS Account select Another AWS account and enter our account ID:
992382634011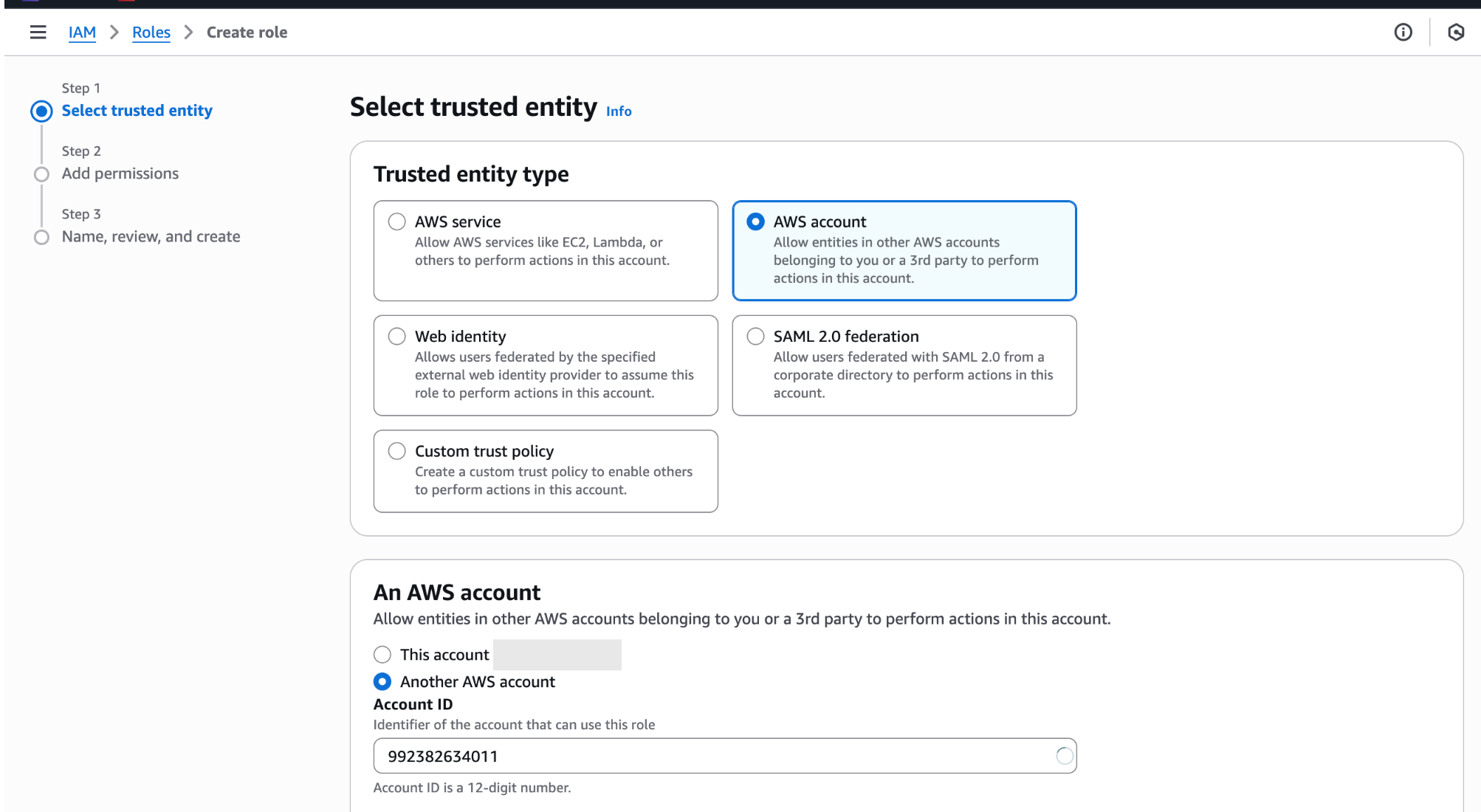
- Under Add Permissions, click Next
- Enter the following as the role name:
cloudglue-external-s3-access-role - Click on the Create role button
- Add an inline policy to the role with the following JSON:
Role Policies
Trust Relationship
The trust relationship is already attached to the role, so you can skip this step.Want to learn more about trust relationships? See the AWS documentation on
trust policies with IAM
roles.
Need help with CloudFormation templates? Check out the AWS CloudFormation
Templates
resources.
Connecting to Cloudglue
- Set up the IAM role using either the CloudFormation template or manual setup
- Get the role ARN from your AWS account
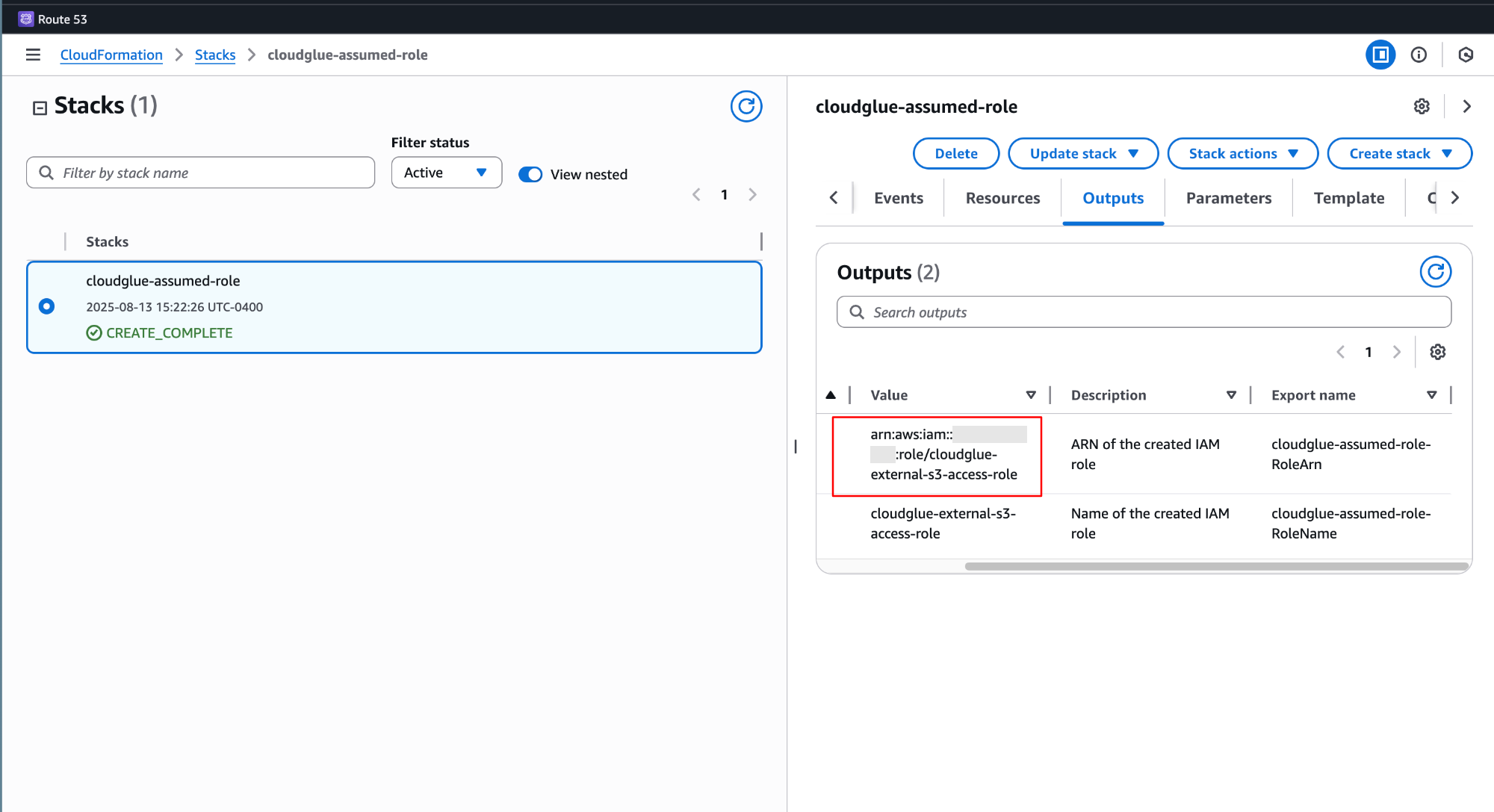
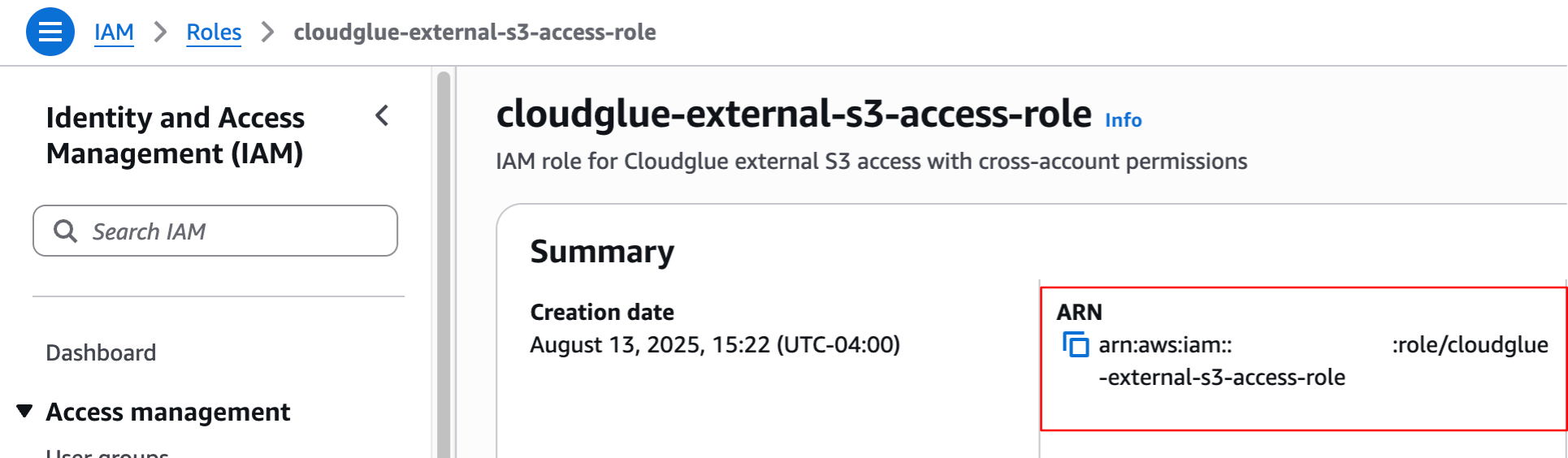
- Configure the connector on our web platform with the role ARN

- Start using S3 URIs directly with Cloudglue endpoints
- Add the external ID that you used in the CloudFormation template or manual setup to the connector on our web platform. This adds an additional layer of security to the connector.
Ready to set up your data connector? Visit our
app to configure your S3
connector.
Need help setting up your data connector? Contact our team directly for
assistance with the setup process.
Managing Access
You maintain full control over your data access. Remove this data connector by doing any of the following:- Revoke access by deleting the IAM role
- Modify permissions by updating the role policies
- Remove connection by revoking the connector on our website
Adding more buckets
If you need to add more buckets to the connector, you can do so by modifiying the policy attached to the role. All you need to do is add the new bucket to theResource array.
How to use your S3 files with Cloudglue
To use S3 files, you can use the s3 URI for a file in your Cloudglue API requests. This would be prefixed withs3://.
Example: